Stego Hunter
Initial reconnaissance
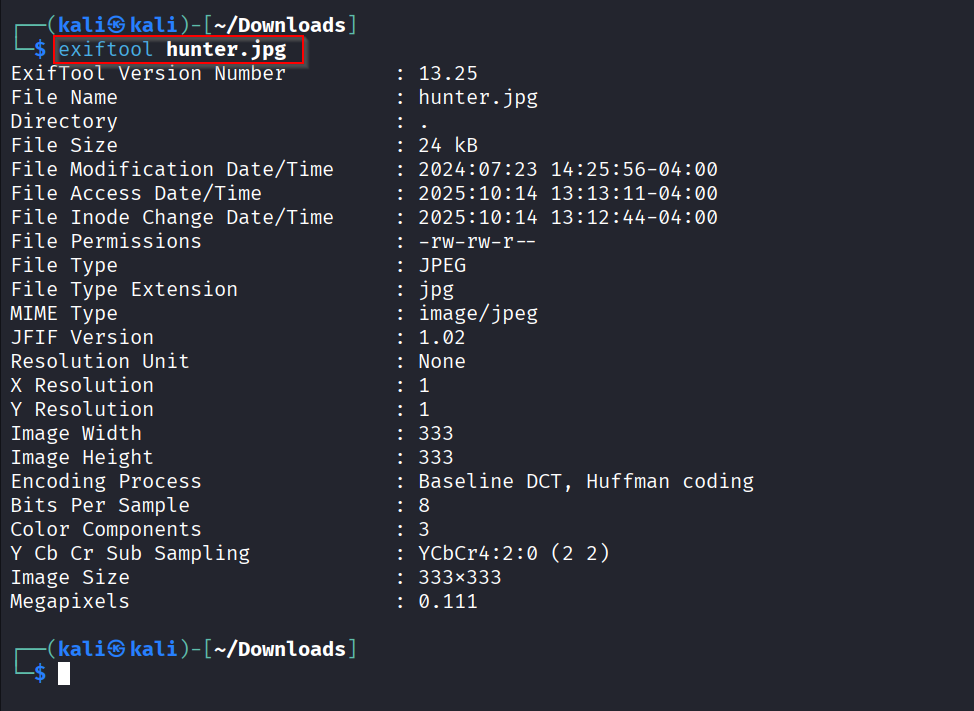
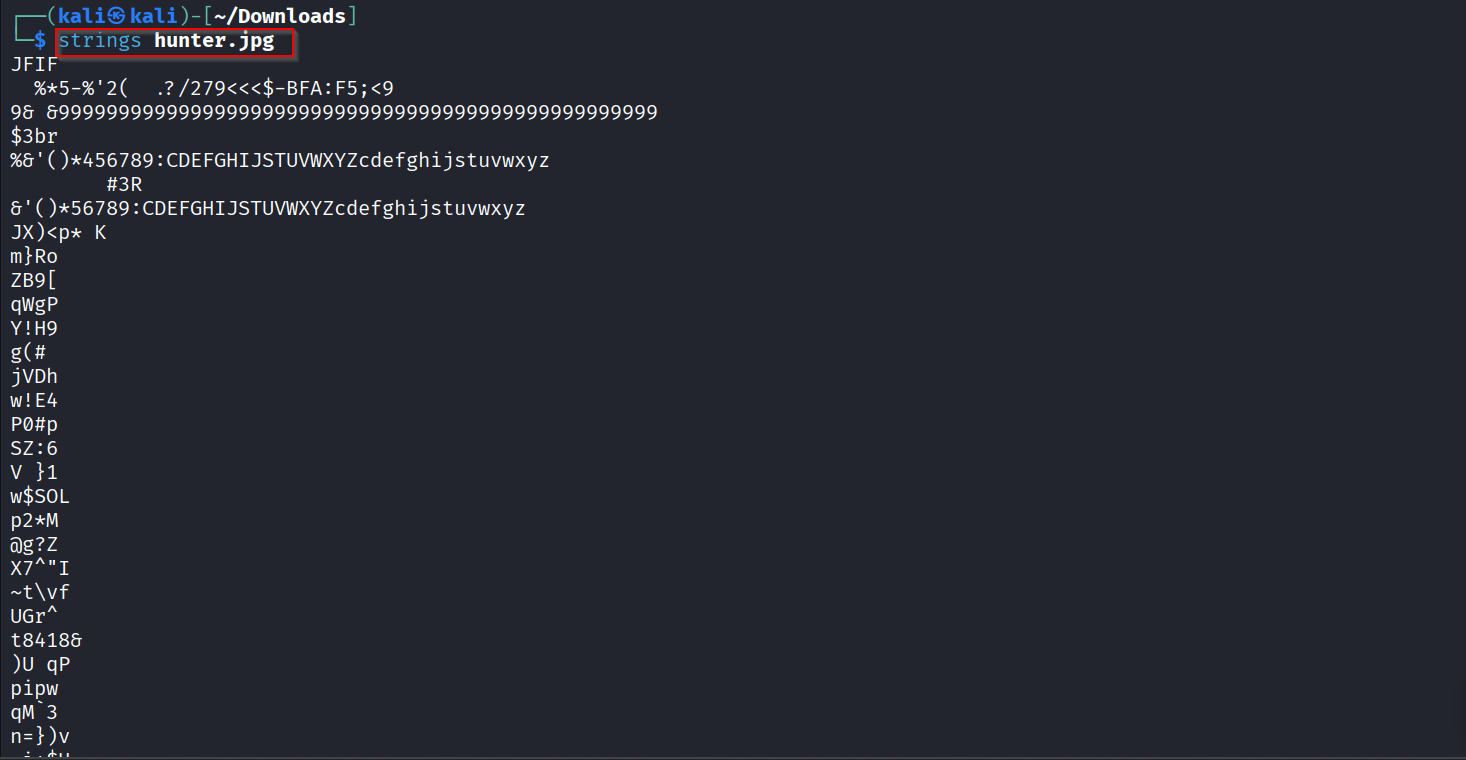
I started by inspecting the file metadata to see if anything obvious was embedded in EXIF or visible comments. I ran exiftool hunter.jpg to check for metadata and then used strings to look for readable artifacts.
I ran: exiftool hunter.jpg, strings hunter.jpg .
The EXIF output showed only normal JPEG fields (dimensions, file dates, JFIF), with no obvious comment or embedded text. The strings output produced many short noisy runs but no flag-like pattern FLAG{…} or CTF{…}, so I moved to stego-specific tools.
Use of stegseek to search for embedded payloads and passphrases
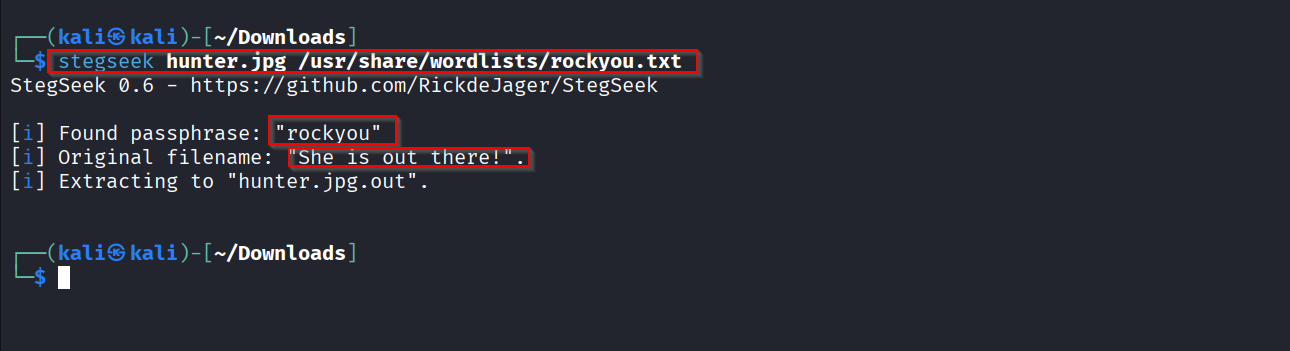
Because strings and EXIF were unhelpful, I tried stegseek with a common wordlist to look for hidden payloads that require a passphrase. I ran:
1
stegseek hunter.jpg /usr/share/wordlists/rockyou.txt
stegseek reported that it found a passphrase and extracted a file. The output included the discovered passphrase rockyou and the original embedded filename “She is out there!”. I inspected the extracted file using cat
Examine extracted blob and decode
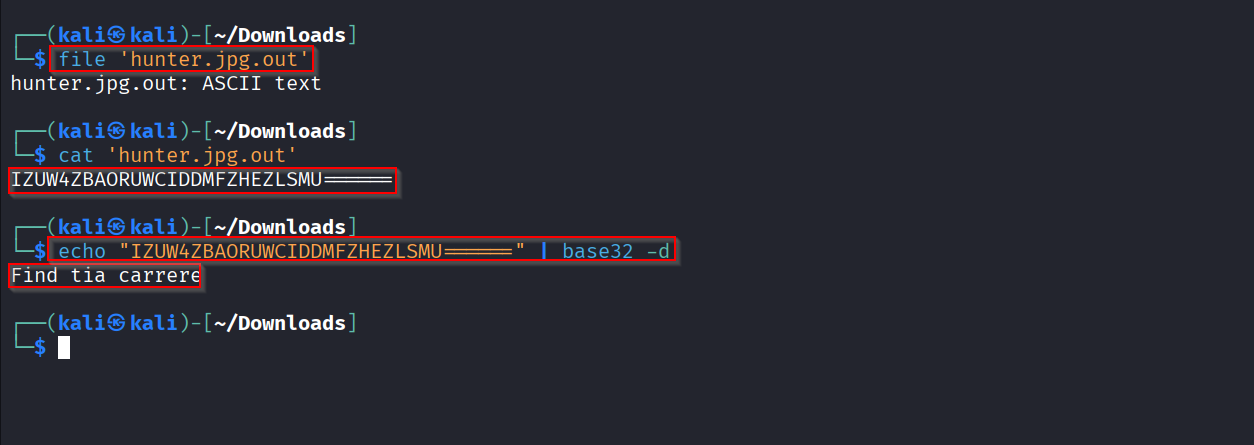
I opened the extracted file available as hunter.jpg.out and printed its contents:
1
cat hunter.jpg.out
it contained IZUW4ZBAORUWCIDDMFZHEZLSMU====== which is base32 encoded. Recognizing the character set and padding pattern, I identified this as Base32. I decoded it using base32 -d. Decoding produced the ASCII string:
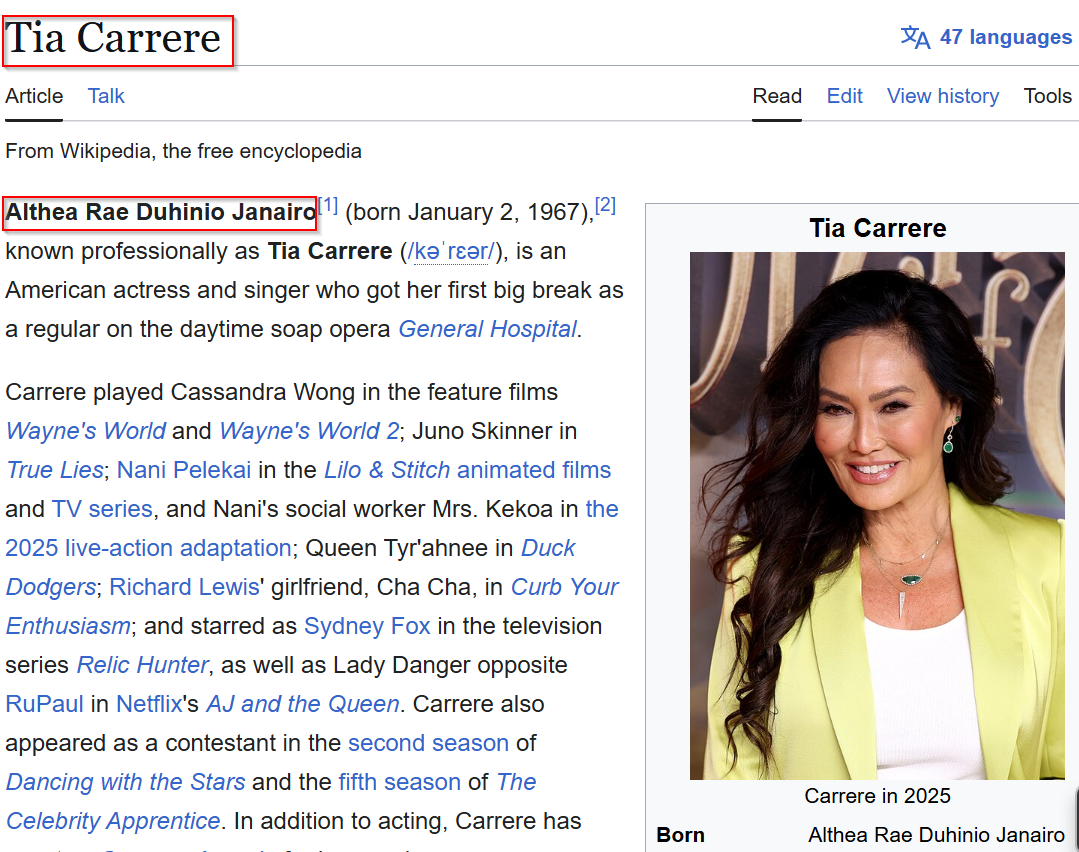
Find tia carrere This was a directional clue rather than a steghide passphrase. It told me what to search for next.
Background research
Using the clue, I determined that Tia Carrere’s full birth name is Althea Rae Duhinio Janairo, which consists of exactly four name parts, matching the expected flag format Flag{Name1_Name2_Name3_Name4}. This name is public biographical information for the actress known professionally as Tia Carrere.
Based on the four-name requirement, I formed the flag as: Flag{Althea_Rae_Duhinio_Janairo}